
Microsoft Has a New Sales Tool Coming This Fall (What Is Viva Sales?)
Business, News, Tech Tips
Microsoft's Viva Sales is a lifesaver for salespeople. Although Customer Relationship Management (CRM) systems make an excellent contribution to the sales aspect of a company's technical support system, its CRMs have limitations. Customer…

5 Ways That Employees Unknowingly Put Your Network at Risk
Business, IT Partner, Tech TipsCompanies often struggle to balance internal security and providing their employees with the resources and network access they need to execute their jobs well.
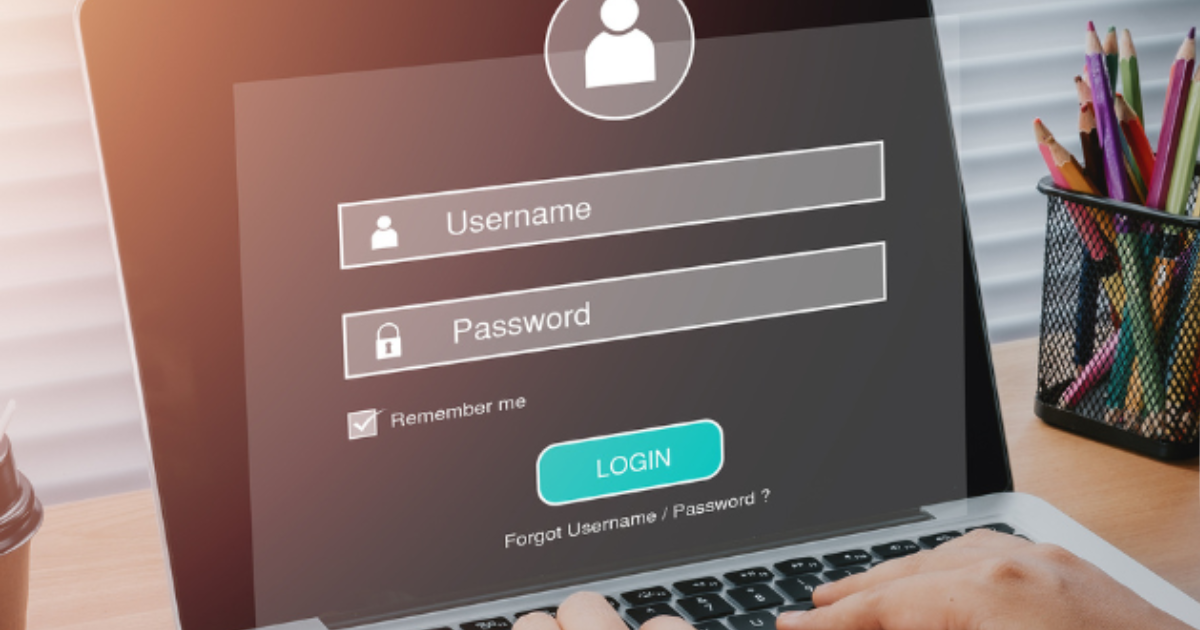
How Do Passwordless Logins Work?
Business, Tech TipsPasswordless authentication is frequently used to strengthen security and lower the cost and complexity of IT operations.

Now That Internet Explorer Is Officially Unsupported, What Do You Need to Do?
Business, News, Tech TipsMicrosoft officially ended support for Internet Explorer on the 15th of June 2022.

Reply-chain Phishing Attacks Are Rising Fast. Here’s How to Protect Against Them
Business, News, Tech TipsWe can show you how to protect your organization from becoming victims of reply-chain phishing attacks and notice the warning signs.

Oh No! I’ve Just Lost My Work Laptop/ Smartphone… Now What?
Business, IT Partner, Tech TipsWe’ll discuss the appropriate steps to take when your work laptop or smartphone is lost or stolen and how you can prevent it.

5 Tips For Creating A Permanent (And Productive) Hybrid Office
Business, IT Partner, Tech TipsMany organizations are adopting the hybrid office. How do you ensure productivity with the on-site and remote employees?

Examples Of Unsupported Technology You Should No Longer Use
Business, IT Partner, Tech TipsWhen new technology comes in, the old tech has to go. Read on to see various examples of technology you should no longer be using.

8 Timely Tips for Getting More Battery Life from Your Laptop
Business, Tech TipsEven if your laptop’s battery life is designed to last 8 hours, the longevity will diminish over time and with use.

Work From Home More Securely by Creating a Guest Network for IoT
Business, Tech Tips The revolution in business that happened over the last two years has altered work habits, making working from home more common.
